Created by the Security Executive Council
This Security Barometer peer poll looked at what security policies organizations have in place and corporate security's responsibility.
Poll question: Which of the following elements are covered by defined policies within your organization.
A. Physical security - e.g., access control, locking, reporting local situations, locking desks/important info. policy:
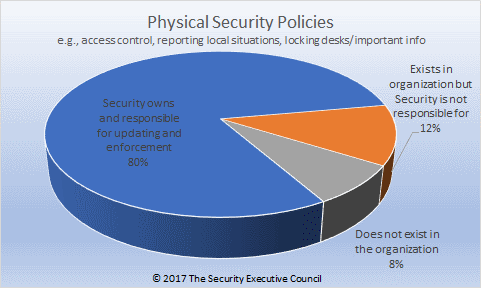
B: Travel policy:
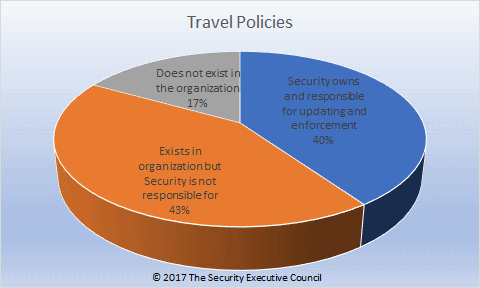
C. Information security policy
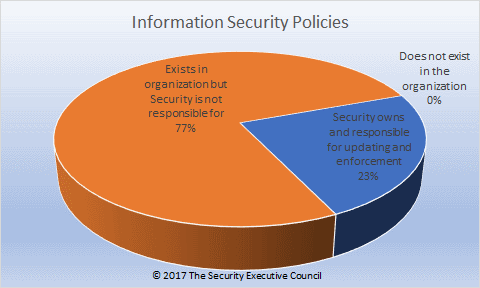
D. Background investigations/vetting policy
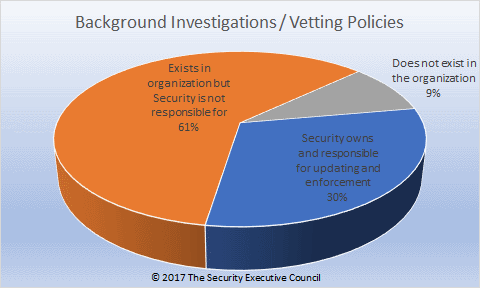
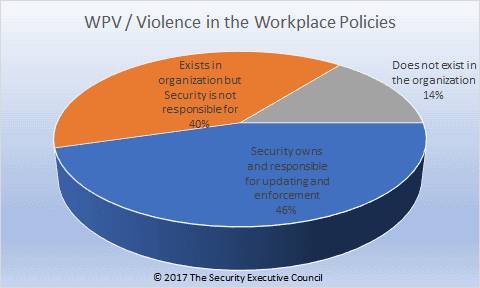
E. Workplace violence policy
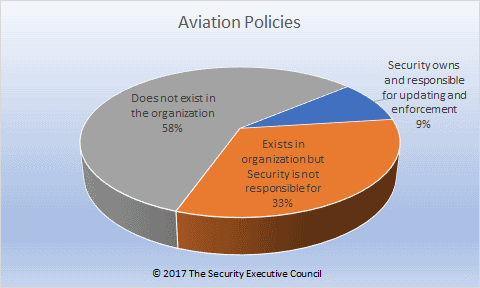
F. Aviation policy
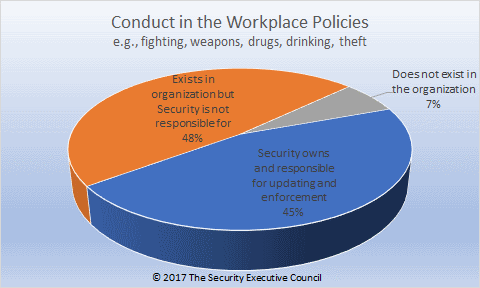
G. Conduct in the workplace policy (e.g., fighting, weapons, drugs, drinking, theft)
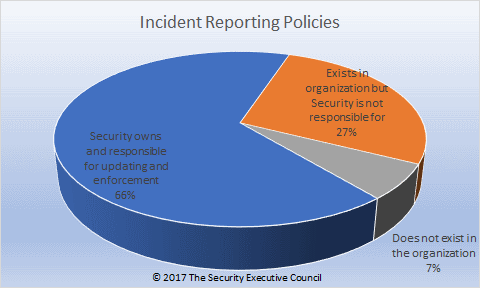
F. Incident reporting policy
G. Other policies
Participants in this survey were given the ability to list policies Security was responsible for within their organization. Some of the policies listed were:
- Policies on use and distribution of Personal Health Information (PHI), restraint of distressed patients, etc.
- Strike/labor disruption protection
- CCTV
- Fraud control
- Working remotely
- Crisis management
- Site suspension policy
- Insider threat
- Authority to search people and property
- Mail room security
- Clean desk policy
- Demonstration and protests
- Business continuity planning
- Financial procedures
- Emergency incident procedures
- Cyber security
- Biosecurity
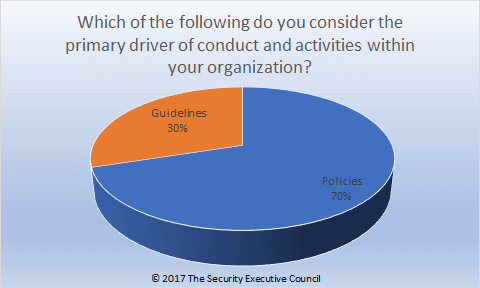
Poll question: Which of the following do you consider the primary driver of conduct and activities within your organization?
Participant Comments:
A large number of participants provided additional comments and clarifications regarding their responses to the survey questions. We selected a few of these comments to share with you. They have been edited from their original to preserve anonymity:
- We are really addressing the fundamental gap in modern organizations. The space between the written guidance (policy, procedures, rules and instruction) and actual practice. Our quest is to make the Policy Manual more than a catalog for "gotcha" and instead ensure that actual practices conform to national/international best practice standards.
- It has been an observation of mine that Human Resources (HR) may take over policies that have traditionally been handled by Security if you, as the Security Professional, allow them to do it. This takes away from the value of the Security Program and is NOT the way to keep a seat at the table with the C- Suite. The senior security leader has to understand and align with the business and advocate for Security to remain relevant.
- Our company is quite policy averse, especially at the corporate headquarters level. We run business using guidelines and individual sites determine where there is a need for policy, as well as enforcing it.
Next Steps
Consider the policies within your organization. What is Security's role and jurisdiction? The SEC can help you create new policies, review existing policies or assist with strategies to enhance policy awareness. The Security Executive Council consists of former leaders of successful Security programs and we can bring that talent together to help you increase Security's standing within your organization.









