The full report is now available here!
Selected Highlights from a Security Executive Council Security Leadership Research Institute Report
In Fall 2021, the Security Executive Council (SEC) partnered with Kennesaw State University (KSU) to begin research on the various forms and structures of collaboration between cyber security and corporate security.
Within the discipline of security, there has been a pervasive belief over the last two decades that the most high-performing and successful functions operate within a “converged” structure, wherein corporate security and cyber security report to a single executive who oversees high-level collaboration on risk issues of both types. It’s often assumed that in this structure, cyber and corporate security collaboration is baked into policies and processes, and the two may share resources and budgets.
In the SEC’s many interactions with security leaders, however, staff and researchers noted that many security functions reach an extremely high level of effectiveness or optimization without such a “converged” structure.
So how does collaboration influence security optimization, and is one structure more likely to lead to optimization than another? Together, SEC and KSU researchers hypothesized that “convergence”- or what they began to call security collaborative optimization (SCO) – exists throughout a continuum of organizational structures.
This research is the initial phase in a multi-part research project.
Methodology
SEC and KSU researchers broadcast a request for participation to thousands of security practitioners, as well as academic researchers and industry partners. One hundred twenty participated in the initial quantitative portion of the research by taking a 26-question online survey. Eighty-eight of those surveys were accepted as usable data.
Then in the qualitative portion, 21 of the accepted respondents were interviewed in depth about the factors that informed their state of collaborative optimization.
Findings
Researchers determined that there are three main collaborative structures. Terminology differed slightly between the survey phase and the interview phase. See below.
|
Question options used in survey question:
|
Descriptions used for interviews:
|
|
Option 1: Merged
|
Merged: Corporate and Cybersecurity are merged into an organizational unit such as a department or division and collaborate on all or most programs and administration.
|
|
Option 2: Separate with partnerships
|
Partnered: Corporate and Cybersecurity are separate organizational units but formally collaborate and partner on all or most routine operational issues.
|
|
Option 3: Separate without routine partnerships
|
Ad Hoc: Corporate and Cybersecurity are separate organization units that do not routinely collaborate or partner on a regular basis but may do so when a situation forces the need.
|
|
Option 4: Other
|
Other: Some other approach.
|
The majority of respondents came from the corporate security realm (rather than cyber or both), and most were from organizations with international operations.
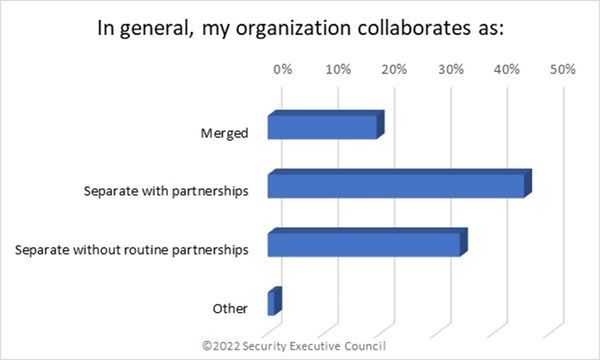
"Separate with partnerships" was the most common collaboration form at 45%, followed by “Separate without routine partnerships”/Ad hoc (34%) and “Merged” (19%).
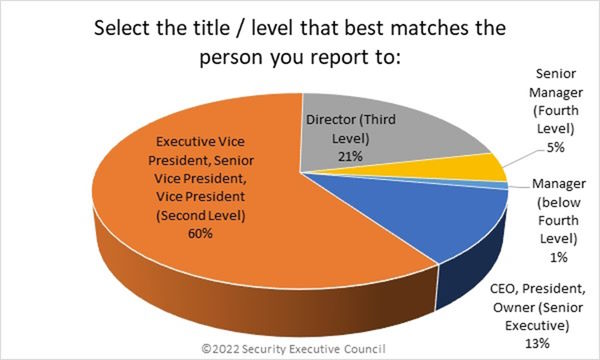
Overall, sixty percent of respondents reported to the EVP/SVP/VP level. Twenty-one percent reported to the Director level, and 13% reported to senior executives.
The full report, available to participants, breaks down reporting levels and reporting domains for each of the three collaboration forms.
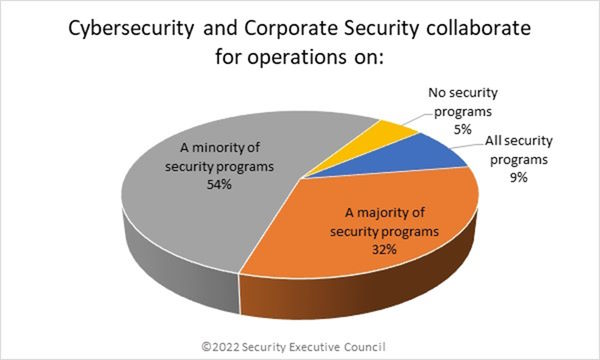
Eighty-six percent of respondents collaborate on operation for some security programs – 54% on a minority, and 32% on a majority. Only 9% collaborate on all security programs, and 5% collaborate on none. The trend is similar for collaboration on administrative tasks.
The full report delves into the traits of the corporate culture in each collaboration form, how risk appetite coincides with collaborative structure, and more.
The subsequent interview portion of this research phase found a number of common themes that likely impact SCO.
Both Merged and Partnered participants noted that good relationships make or break collaboration, regardless of whether the structure mandates collaboration.
In a similar vein, transparency and strong and regular communication are vital. It’s important to bridge gaps in terminology and language to understand other views and perspectives.
The structural shift toward a more collaborative form generally occurs because of an unexpected organizational change, such as the introduction of a new leader, a corporate acquisition or spin-off, or a negative security incident.
The value of security collaborative optimization is difficult to measure, according to participants. It’s not as often found in dollars and cents as in speed and agility in identifying and responding to incidents.
The full report goes into more detail on each of these points and delves into lesser similarities as well.
Next Steps
Phase 2 of this research will consist of a series of panel discussions with practitioners to focus on SCO outcomes and to ensure that cyber security leaders’ perspectives are equally represented in the research.
We are grateful to Kennesaw State University and to all the practitioners who have participated thus far. Unless security leaders are willing to share their experiences and data, quality research cannot be conducted.
Contact us if you are interested in participating in Phase 2 of this research project.
You can download a PDF of this page below:



