Corporate security leaders frequently urge employees, stakeholders, and other security service users not to become complacent in their role in protecting the organization. It’s the cornerstone of every awareness program and the mantra of many an executive briefing: The fact that we haven’t had an event/breach/crisis doesn’t mean we don’t need to continue to be on guard. It means the opposite – that our vigilance is working.
However, how often do security leaders internalize this advice when it comes to managing the business of security?
Do you get so mired in the day to day – paperwork, meetings, dealing with incidents – that, for time’s sake, you seldom take a step back to look at what Security is doing, how it is performing, and whether it’s meeting the organization’s needs?
Do you assume that because management hasn’t asked much of you, that the function is doing all it can and should be doing for the business?
Many security leaders fall into patterns of complacency at some point in their careers. If you’re lucky, you’ll recognize it yourself and find a way to open up more time and attention for big-picture issues.
If you’re not, that realization will fall on you when your boss suddenly asks you to explain why your function is doing what it’s doing, what it costs, what it saves, whether it’s too much or not enough, and with data, please, to back up your statements. Maybe the questions will come after an incident, before a merger or acquisition, after the replacement of the CEO, or when the organization begins a continuous improvement process.
Regardless of the reason, it will be difficult to be prepared for this conversation if you don’t engage in any type of continuous improvement yourself.
Continuous improvement processes – of which assessment is a component – have myriad benefits beyond preparing a function for a management inquisition. By reflecting on processes, identifying inefficiencies, and setting goals for incremental change, a security function can amplify its value, lower cost, better engage its workforce, improve protection and risk management for the company, and boost internal customer satisfaction.
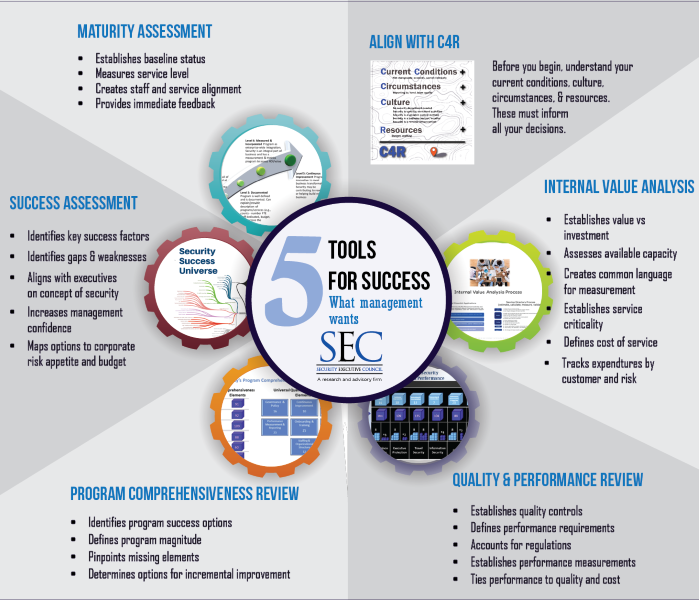
Assessment is the first step in most continuous improvement processes, and there are a variety of ways to do it. Here are five assessments the SEC has developed over the years to help security leaders reflect on their functions and find ways to improve.
Types of Assessments
The Security Executive Council has worked with practitioners in many industries, combining the collective knowledge of successful former security executives with corporate-security-specific research to develop several assessments for different facets of the security function. Each one helps the security leader identify the function’s current state, pinpoint gaps, identify options, and communicate the way forward.
 Security Success Universe Assessment
Security Success Universe Assessment
The SEC’s Security Success Universe Assessment is a high-level analysis meant to show security leaders what is possible for their function. It can help expand your thinking about what you do and what you could do, can help find and analyze gaps, and can ensure your program is balanced and complete.
The SEC Security Success Universe is based on more than 15 years of research into successful security programs and leaders. It outlines 115 elements in 13 categories that can help the security leader down the path to excellence.
By working through these categories, security leaders can identify the key success factors that will best serve their function and organization and then map their options to the organization’s mission and risk appetite.
This requires invaluable conversations with executive management on the organization’s concept and understanding of security, its expectations, and goals for alignment and optimization.
This assessment opens the door for executive input and helps establish a common language and concept of security with executive management. It leads to more comprehensive, tailored risk management for the organization, as well as increased visibility of and confidence in the security function.
Maturity Assessment
The Corporate Security Maturity Assessment examines the function in a narrower frame. It is a particularly useful tool for security leaders who are asked where their security function stands in comparison with others.
Benchmarks and peer comparisons are useful to an extent, but the diversity of organizations, structures, service models, budgets, and even definitions of security among executive leaders make apples-to-apples comparisons extremely difficult. Instead,
the Maturity Assessment compares security against a standard: a stable maturity model framework developed based on the Security Leadership Research Institute’s corporate security research.
Like other maturity assessments, the SEC’s measures growth or evolution across a spectrum, from informal, to managed, to measured and effective, to optimized. The assessment is specific to corporate security programs. It measures the maturity of the function’s governance and procedures, risk tracking and assessment, standards of competence and staffing, among other factors.
It’s important to note that the spectrum is not a grade or a ranking; some organizations may want and need a program on the less formal side of the spectrum, and others may need one that falls nearer optimization. Determining where you are on that spectrum now allows you to work with management to determine the level of maturity that’s appropriate for your organization, to strategize budget and resource allocation for that goal, to set progress milestones toward that level, and to track program development against a timeline.
Program Comprehensiveness Assessment
SLRI research has shown that global CSOs have responsibility for anywhere from five to 24 common programs with security implications, from facility security and background vetting, to resilience, to investigations and fraud prevention. How complete is each of the programs you own?
The Program Comprehensiveness Assessment draws on SEC research into the various domains and elements of security. For each commonly security-owned program, SEC subject matter experts have identified a collection of elements that constitutes program comprehensiveness. There are 60 elements that make up a comprehensive investigations program, for example, and 124 for comprehensive event security.
Recognizing elements that may be missing from any given program is the first step in incremental improvement, and the assessment further assists security leaders in integrating missing elements into their programs.
Program Quality and Performance Assessment
The Program Quality and Performance assessment helps answer executive questions not about what the security function is doing but about how it is doing it, and how well.
This assessment looks at eight categories of the security program, setting performance requirements, metrics, and quality controls for each. Performance requirements can be driven by regulation and existing policy as necessary.
Continuous improvement and staff development goals can be tied to the results, as can resources. With this assessment, the security leader can find, track, and correct weaknesses in quality and performance and assure executive management of security’s commitment to excellence.
Internal Value Analysis
In a 2016 SEC poll, a majority of security leaders answered that the business value of security is the most important concept they need to communicate to management.
Further research has continued to bear this out. The Internal Value Analysis provides concrete data on business value and a framework in which to present it clearly and effectively.
Analyzing the function’s capability and capacity clarifies its contribution to the organization. This assessment identifies and categorizes security services and FTE time dedicated to each; matches these services with the risks they reduce; ranks the criticality of the risk; and connects security services with the business units that use them.
While all the assessments we’ve discussed here have been specific to corporate security, this one is most similar to the type of assessment a non-security third party firm might conduct of all business functions at the request of management. One of the benefits of this version is that it is developed and conducted by corporate security experts who are familiar with the unique needs and challenges of security as a function.
Each part of the Internal Value Analysis answers a common question posed by executives. It lays out the value the organization receives for its investment in security; assesses the capacity of the function; defines the many internal users of security services and programs; eliminates redundancy; and calculates the cost of security services.
Being able to point to this data and present it quickly when – or before – requested will build executive confidence in the security function and in you as a business leader. It will also increase the organization’s understanding of security services and the function’s risk mitigation impact.
Assessment Outcomes
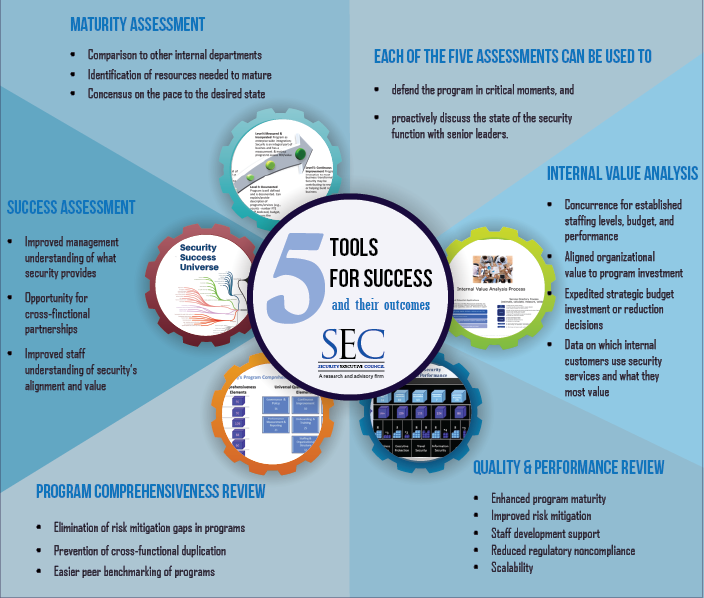
Each of these assessments is a valuable tool for discussing the state of the security function with management. You can proactively assess the function in any of these ways and then bring the results to company leadership before they have to ask for them. Doing so will show your executives that you recognize the elements of a strong program, that you are determined to be a good steward of company resources, and that you are constantly working toward improvement. They will see that you are engaged in not only good security, but good business program management.
Ready to move forward?
Contact us to set up an assessment today.


