Created by George Campbell, Security Executive Council Emeritus Faculty
Scratch the surface of any major business today and you will likely find not one homogeneous, wholly owned structure, but a set of interdependent alliances based on contracts, ownership shares or other ties to the mother ship. Long before the press conference or public notice announcing these alliances, auditors, mergers and acquisitions magicians, purchasing specialists and a gaggle of lawyers are at work (at huge expense) assuring your company’s executives that this arrangement equates to a 1 + 1 = 3 result.
Is Corporate Security on the team?
This process isn’t about selecting an ad agency or real estate company. It is about business activities that are at the core of the business and shareholder confidence. These marriages or outsource relationships may provide external entities with virtually free access to proprietary business methods, trade secrets or sensitive customer information. They may be in high-risk locations with notoriously unreliable infrastructures. The list of risks is directly proportionate to the criticality of the product or service sought in the proposed relationship. The awareness of those risks is directly proportionate to the degree to which qualified sources are engaged to proactively identify them. Security needs to be an integrated member of the due diligence team.
The chart that follows examines the potential risks involved in an acquisition being considered by a fictional company. What can we learn from this examination?
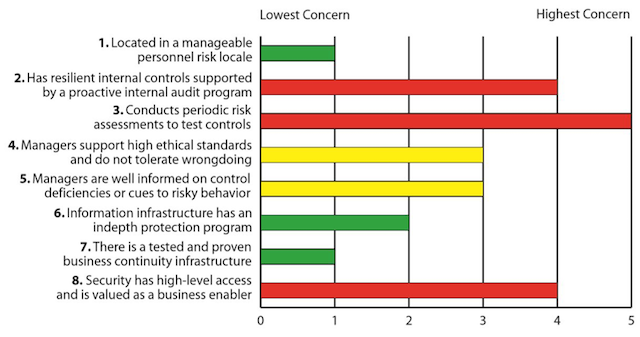
The chart displays eight factors that the security organization has vetted in its evaluation of the prospective business alliance. The following conclusions were formed by an on-site security review team formed specifically as an integrated part of the due diligence team. Management recognized that this aspect of risk analysis was a critical element of the decision on this project. The target company had no choice but to allow a complete and honest review and, as a result, emerged from the process with several vulnerabilities addressed.
1. Personnel risk was evaluated through benchmarking with security colleagues with a presence in the area of the targeted business. Location risk is nominal.
2 & 3. The resilience of internal controls and objective analysis of risk are keys to reputational risk management and are the best defense against wrongdoing and poorly managed business processes. These aspects of the assessment show a lack of knowledge of the adequacy of controls and are clear red flags for this potential acquisition.
4 & 5. Not surprising given the apparent status of the last two factors, Security also has serious concerns about management’s understanding of and commitment to high ethical standards. The lack of strong probing on the adequacy of controls combined with this apathy makes it clear why managers are not well informed on risky behavior.
6 & 7. The information risk management infrastructure appears sound, with strong, up-to-date controls in place. A knowledgeable team manages the business continuity program.
8. Finally, it shouldn’t be surprising that this company’s security organization lacks influence and access.
This examination indicates significant risk in this potential acquisition. Due to the criticality of those factors of highest concern, Security’s recommendation will be to walk away. There is far too little concern for doing the right thing in this target.

