Created by George Campbell, Security Executive Council Emeritus Faculty member
 Objective:
Objective: To visually convey our understanding of and response to a risk event, to show how that risk links to applicable metrics, and to demonstrate that measures are being taken to mitigate future risk.
Results Sought: There are multiple advantages to this type of presentation.
• You inform management in a way that demonstrates the competence of your lessons-learned analysis;
• You influence change by assigning accountability both for contributing causes and follow-up actions; and
• You provide benchmarks for assessing the quality of proposed countermeasures.
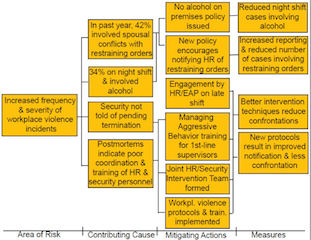
Where is the data? You will need to find data that will help you objectively identify the causes (not symptoms) of the risk event, select the best means to better prevent and/or respond to a similar event in the future, and measure the effectiveness of each of the selected countermeasures. In the nearby graphic example, the incident postmortem uncovered the data listed as Contributing Causes, and each of the selected countermeasures in the Mitigating Actions column have an associated metric in the Measures column.
Risk Management Strategy: We have limited time with senior management, so we need creative ways to influence change, to inform and demonstrate our competence. The “measures map” above is a visually engaging method of presenting findings from an incident postmortem. It enables measurement of performance, status and cost tracking during the reporting process. It is also a useful way to brief constituents or staff on a proposed risk mitigation strategy. Build the map collaboratively with affected business unit personnel and other governance team members as you walk through the incident postmortem. This demonstrates corporate leadership and more clearly influences accountability for successful risk management going forward.
It is wise to periodically evaluate a variety of post-incident maps to identify common causes and opportunities for selecting countermeasures that may beneficially impact multiple business process vulnerabilities.

