Created by George Campbell, Security Executive Council Emeritus Faculty member
The Objective: To identify security-provided products, services and positive results that help meet the enterprise’s business goals.
Results Sought: Increased understanding and appreciation by senior management and other key stakeholders of security’s value and contribution to the bottom line.
 Risk Management Strategy:
Risk Management Strategy: How effectively are we aligned with the businesses we serve? How do the organization’s business executives perceive the value of the security function? Security leaders must use multiple data sources and metrics to identify and communicate security’s positive impact on the business and its bottom line.
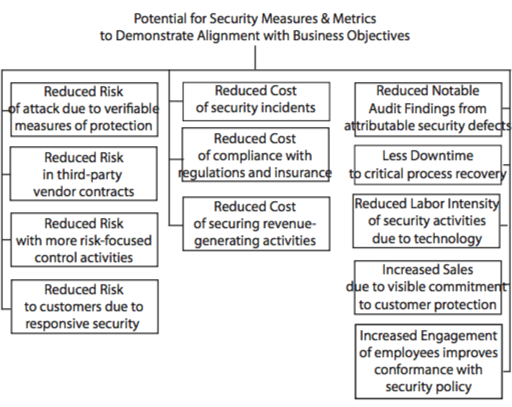
Here are some examples you may be able to identify in your own organization:
• Penetration testing should yield data on the effectiveness of safeguards and support claims of reduced opportunity for attack.
• If our pre-contract examination of the risk potential of third-party vendor relationships identifies vulnerabilities, we can develop contract terms and post-contract inspections that reduce risk and consequence of loss.
• By examining incident trends and incident postmortems, we can produce metrics that either affirm the effectiveness of internal controls or justify the redirection of resources, yielding improved risk management practices.
• If we develop metrics to measure the resilience of our protection of confidential customer information, the results may clearly show security’s contribution to customer and shareholder protection.
• Through focused metrics on the effectiveness of safeguards, we can generate evidence of cost reduction through reduced consequences of risk and reduction in insurance premiums.
• Metrics associated with fast recovery from business interruption incidents consistently show the advantages of a resilient business continuity program.
• Virtually all of the post-9/11 security-related regulations impose metrics to provide verifiable measures of compliance and thereby minimize the imposition of fines or other impact to shareholder value.
• When we implement new security measures, we may show value by comparing pre- and post-implementation incident rates and costs.
• Advertised and demonstrably effective security measures not only enable customer satisfaction but may also be a draw for new customers and sales. Being “the secure choice” is a plus to the bottom line.
• Deployment of proven security technology consistently demonstrates the potential for reduced cost of security operations. The return on investment for an access control system that eliminates “x” manned security posts is a frequent example.
If you have the opportunity to present to management on the value of security, be sure to carefully identify only the results or functions that reliably offer support to your program. The key is to determine which metrics will best demonstrate your clear connection to the objectives of the enterprise you serve.

