Created by George Campbell, Security Executive Council Emeritus Faculty member
We have mentioned balanced scorecards and KPIs, but it is useful to occasionally revisit these concepts because they can be so much a part of a corporate management business strategy. In our corner of the business, we may employ KPIs in any of several security program areas.
Objective. Organizations use key performance indicators to evaluate their success in reaching long-term organizational goals. We may use them to set specific, measurable objectives for program performance. They may track our success in engaging the business in improved security practices or the progress of vendors in meeting contractual performance specifications. They may set standards for incident response and resolution or any number of desired outcomes tied to the allocation of security resources.
 Strategy.
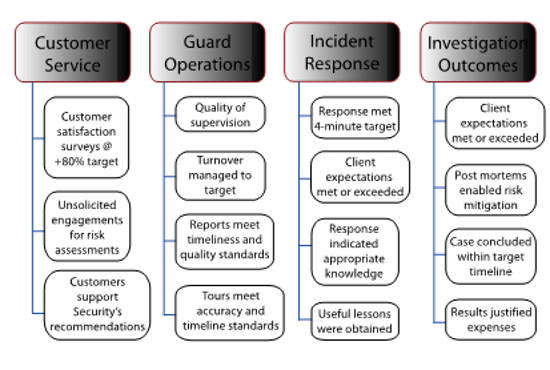
Strategy. In the example above, the security manager has chosen four areas of program performance by which to assess his department’s operations for the year: customer service, guard operations, incident response and investigation outcomes. Under each, the security manager has identified multiple measures he will track to indicate success in that sector of the business plan.
Customer Service. He has set an 80-percent customer satisfaction target that may be measured by post-incident feedback, specific survey exercises or as part of routine one- on-one customer meetings. Additionally, where business units request unsolicited risk assessments and implement a targeted percentage of Security’s recommendations, we have clear evidence of solid customer service and alignment with the business.
Guard Operations.Guard force operations typically take up a substantial part of the security department’s budget. This security manager contracts with an outside vendor, so he faces issues of liability, co-employment and vendor performance in an industry with frequently high-turnover employment pools. It makes sense to set measurable contractual expectations such as those found in service level agreements (SLA). Our manager has selected four measurable SLA criteria dealing with supervision, turnover and daily competency — each of which contributes to a qualitative picture of vendor performance.
Incident Response. Targeting high-impact performance indicators in this area is a virtual imperative for a security program. Our security manager has set a response time standard that clearly reflects attention to safe and secure workplaces, and he has also identified measures of security team knowledge and customer responsiveness and the highly valued, actionable lessons-learned from incident post-mortems.
Investigation Outcomes. Throughout this landscape of performance indicators, we see our security manager’s attention to customer service, here with feedback on client expectations — a potentially sensitive area depending on the implications of investigative findings and results. There is also a continuing focus on management competency, as seen here in the measurement of case duration and cost assessment, as well as the opportunity to contribute to improved risk management through the investigative post-mortem process.
If you are not measuring, you are not managing. We must embed in our minds the imperative of connecting measurable results — critical success factors — with security program objectives. Key risk indicators and key performance indicators need to be the common tools you reach for as you craft the content of your various security programs. They serve to help you navigate the dynamics of risk, better connect and align with the business and its leaders, and effectively manage the often limited resources available to protect the enterprise.
For more information on Key Performance Indicators see
Security Metrics: Measuring Performance
Watch our
3-minute video to learn about how the SEC works with security leaders. Contact us at:
contact @secleader.com.
Copyright Security Executive Council. Last Updated: July 18, 2017
You can download PDF of this page below:

